If you are using Bitlocker, Configuration Manager 1610 or higher and get a piece of hardware that has TPM 2.0 there are a few more hurdles to get the device encrypted. Coretech has written notes from the field which states the two options going forward. Following their recommendation – lets go down the path of running a device with CSM (UEFI) enabled and installing Windows 7.
Make sure that the device is running in UEFI and is setup as expected. I will leave the actual configuration of BIOS / UEFI out of this – as any device with TPM 2.0 will most likely have a preconfigured settings that are optimal. If not, time to configure for UEFI (without Secure Boot).
UEFI Boot
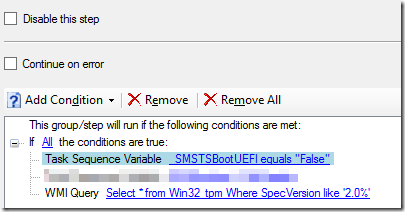
Once that is completed – create a new group that has the intention to identify if we (if possible) booted with a legacy option (legacy PXE-boot, legacy USB stick etc etc). Validate that its not UEFI-booted and that we have a TPM 2.0 chip (and add a check that we are also intending to install Windows 7 x64).
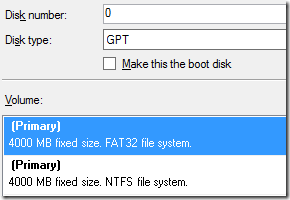
Only two steps are required in the group – format the drive as GPT and then a restart to the boot-image. Suggested format:
Preprovision
Once we have ensured that the device is running in UEFI, and not legacy…, and since we all are running a newer ADK then 1511 – we should add three registry keys per Microsoft
Above configuration of the algorithms for Windows 10 (build 1511) is kept as REG_DWORDs under:
HKLM\SOFTWARE\Policies\Microsoft\FVE
Operating System drives: EncryptionMethodWithXtsOs
Fixed Data drives: EncryptionMethodWithXtsFdv
Removable Data drives: EncryptionMethodWithXtsRdv
Hotfix
You can integrate the TPM 2.0 hotfix into the Windows 7, or simply install it after the WIM has been copied onto the machine. It should be installed before MBAM (or just bitlocker) is installed and starts handling the encryption